Is Security Awareness Training Failing Us? The Stats Are Proof
November 16, 2022 | By: Stephen Boals
The Phishing Statistics
I read a research report published by a large US-based Security Awareness Training company this morning (who I will respectfully not name because that is not the point of my article), and the stats they reported made me scratch my head in wonder: Can generic, content-based training ever conquer all the variations and complexity of various types of phishing attacks effectively? Here are the statistics from one section of the report, based on 600+ security professionals and 3,000+ end users. Let’s focus on the US numbers.
- 100% of the organizations polled said they provided cybersecurity training for their users.
- 79% said they had at least one successful phishing attack.
- 40% reported at least one successful ransomware attack.
So, obviously no single intervention can ever claim to reduce the risk of a cybersecurity attack to zero, right? There will also be some risk. But considering those numbers above, how in the same survey did 84% of those same respondents then report “their training programs are working, based on reduced attack numbers”.
Something is obviously not right. If you are using the same training and it continues to result in high levels of failure, how can we claim our training and phish testing methodologies are adequate? Perhaps the problem is that phishing is only a proxy for the real thing and some bias in our phishing simulations are not replicating real world attacks? Or, are we simply accepting sub-optimal results and hoping for the best because we feel relatively this is the best that we can do? Or maybe this is why so many organizations are skeptical that their investments in security awareness training even represent a good investment because, relatively speaking, even with broad training, successfully human-factors attacks continue to rise every year? Should we even bother?
This Must be Fixed?
The short answer is yes – we must bother. But perhaps we need to reconsider our whole paradigm of security awareness training to fix it? I think the question should be: What is the lowest possible level of risk we can attain with training? Here is a proven path to fixing a sub-average phishing and awareness programs, using novel methods that are quite different and will deliver a maximized risk adjusted ROI.
- Disconnect Training Vendor from Phish Simulation. – There is bias in any training system. And if the trainer also writes the assessment/test, then it’s really like the fox running the hen house. They teach to the test and not to real risk! That is no deception or mal intent implied in this conclusion; it’s just the nature of the beast when you design both products. You will get employees tested on what they believe is important within their content and training. This reduces the effectiveness of phishing detecting risk.
- Add a behavioral science layer. You cannot train the end user on all the possible content permutations of socially engineered attacks. Or teach “one size fits all rules” that do not consider a person’s role or job requirements. The bad guys are getting smarter and smarter by using advanced, evermore complex and now hybrid methods of attack to lure your users to the click. Therefore, you need to build resilience and awareness in users that build their judgment and capacity to avoid these attacks. This is not about training, rather it is about educating users using behavioral science methods curated to personality, learning preferences, job context, existing knowledge and propensity to click. We need to teach users not train them because knowing something is not the same as doing something. This immediately begins not only to lower phish-prone behaviors but also the risk of a successful attack, period.
- Use an experimental model to verify impact. In any scientific study, a control group is used to establish a cause-and-effect relationship by isolating the effect of an independent variable and then examining results. This helps us continually improve our interventions by proving they are effective. Researchers then change the independent variable in the treatment group and keep it constant in the control group to assess the actual rate of effectiveness versus the assumed rate. Different approaches will work more effectively than others, and they need to be identified and then incorporated into your security program to improve its effectiveness. If you run any type of proof of concept with an advanced or layered cyber solution, insure you leverage two randomly chosen test groups to examine the impact of any 3rd party intervention and then retain only those that actually reduce your risk, not your imagined, risk of an attack.
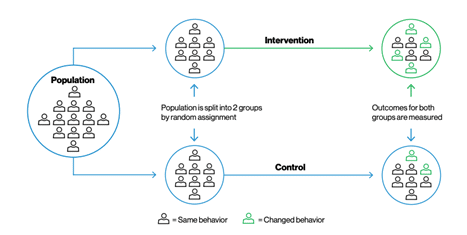
Always use randomized tests with control groups (Verizon DBIR, Changing Behavior)
- All the gains are in the Last Mile. A few numbers to start:
-
-
- Organizations with no Security Awareness Training typically have a 30%+ phish failure rate
- The average phish failure rate after training is 16.7%
-
By deploying our patented Human Defense Platform, we see phish rates below 2%, with benchmark clients getting in the sub 1% range over a 6 – 12 months. By the way, these are not our results – these are results of independent client studies as noted above. These gains are driven by a science-informed methodology that includes the following phases:
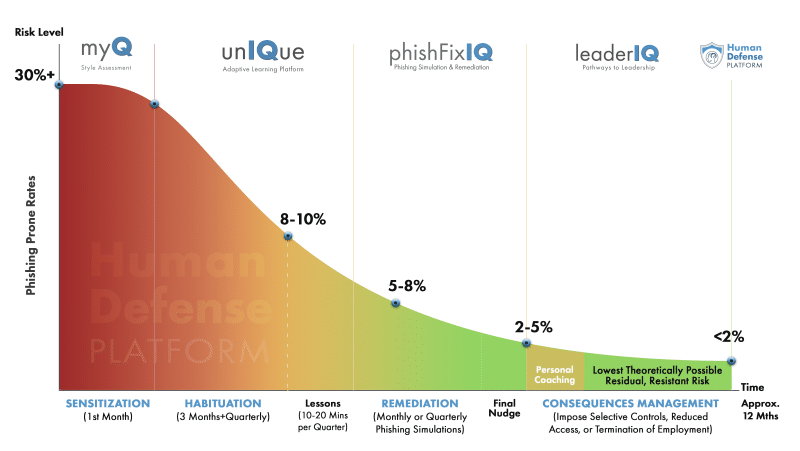
Our patented process for maximum reduction of human risk
- Sensitization – leveraging our patented behavioral science approach, the first phase introduces the vulnerabilities certain risk-styles may be exposed to based on their personal risk-rule attributes. This leads to instilling new planned responses to overcome their instincts and impulses and is the foundation for positive behavioral changes.
- Habituation – this phase picks up at the edge of sensitization, and through timely exposure to both personalized training and phishing simulations, any response to targeted attacks begin to decrement. This is the phase with the greatest change in failure rates.
- Remediation – you will have failures from your phishing simulations, and how you handle them is critically important to the lowering of risk. The standard solution is to dish out more training, or the same exact training and content out that let them get phished in the first place! That is not remediation, it is repetition and is of no proven value. Providing a curated remediation module based on personality traits and specific vulnerabilities tied to risk profile will actually remediate this tendency prevent long-term recurrence. In most of our studies, we can remediate 95% – 100% of serial “clicksters” in one pass. Can your existing training regime accomplish that level of remediation?
- Leadership/Coaching – Is your leadership/management team armed with the process and methodologies to coach those that are not meeting the mark when it comes to consistent improvement in their security habits? Training should be part of an overall program to drive a cyberaware culture that goes way beyond simply avoiding phishing to creating a security centric culture everywhere and all the time. Immature or overly simplistic training cannot accomplish the same impact as an improved tone from the top that makes security top-of-mind.
- Consequences Management – So, you have a managing director or a cardiologist or some other high value individual that just keeps missing the mark. Imposing selective control, reduced access or other restrictions is the final level of risk reduction when you are certain that training will not change their online behavior. This group of change resistant risk are the residual number of people that represent the most organizational risk. Can your existing training clearly locate and identify those people so that you can intervene differently? What specific security-informed practices are in place to handle these outliers? If not, your program is not optimized for maximum impact.
Next Steps
All these steps can bring you to what we call the Lowest Theoretically Possible Residual, Resistant Risk by improving the maturity and impact of your security training investment. Stop training and start educating your users profoundly differently to achieve a real reduction in risk that will measurably improve your risk posture.
Want to take your cyber culture and training program to the next level? Call us today for an intro to our Human Defense Platform.

